Edgio requires a TLS certificate hosted on our network to serve HTTPS traffic for:
-
Your Hostnames: You may either:
-
Edgio Domains: Edgio provides a wildcard TLS certificate for the domains that we automatically generate when you deploy to your property. This certificate is managed by Edgio and it does not require configuration.
Sample domain:
my-team-my-site-feature-a-1234.layer0-limelight.link
Autogenerating TLS Certificates
Edgio can automatically generate TLS Certificates on your behalf using Let’s Encrypt. These certificates are free, valid for 3 months, and automatically renewed as long as the following technical requirements remain met:
- Hostnames: Register the hostnames that will serve traffic for each environment.
- Certificate Authority Authorization: The Let’s Encrypt certificate authority (CA) must be allowed to issue certificates for each registered hostname.
- Domain Control Validation: Prove your control over that domain by adding an
_acme-challengeCNAME record to it.
Certificate Authority Authorization
The Let’s Encrypt certificate authority (CA) must be allowed to issue certificates for each registered hostname. It is allowed to issue certificates when either of the following conditions are true:
-
A CAA record has not been issued for that hostname or a parent hostname (i.e., the main domain or at any depth of subdomain). This DNS configuration means that any CA is allowed to generate certificates for that hostname.
CAA validation follows CNAME records. For example, if your
www.example.comCNAME record points towww-origin.example.com, then the CA will first request CAA records forwww.example.com. Upon detecting a CNAME record, it will request CAA records forwww-origin.example.cominstead. -
A CAA record explicitly allows the Let’s Encrypt CA to generate certificates for that hostname.
This sample CAA record indicates that the Let’s Encrypt CA is allowed to issue certificates for
cdn.example.com:cdn.example.com. CAA 0 issue "letsencrypt.org"
To add a CAA record to allow Let’s Encrypt to generate certificates for your domains
-
Verify the value of the CAA records for your domain from the command line.
Bash1# Run the following command2dig caa +short <your-apex-domain>34# Example5dig caa +short mywebsite.xyzThe following sample response for a CAA query shows that only specific CAs are allowed to generate certificates for that domain:
Bash10 issue "amazon.com"20 issue "digicert.com"30 issue "globalsign.com"40 issue "letsencrypt.org"If the result of the CAA DNS query is empty, it means that any CA is allowed to generate certificates on that domain. If so, proceed to domain control validation.
-
If there are
CAADNS entries defined on your hostname or parent hostname, and if the Let’s Encrypt’s CAA entry is not among those, you will have to add an additionalCAAentry for Let’s Encrypt.From your DNS service provider, add the following
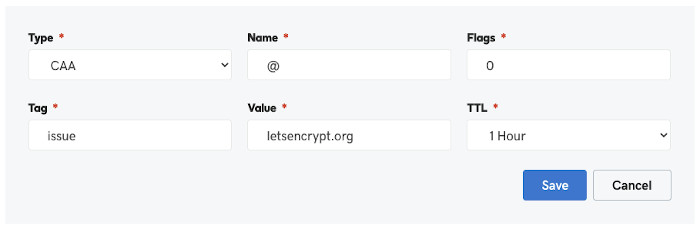
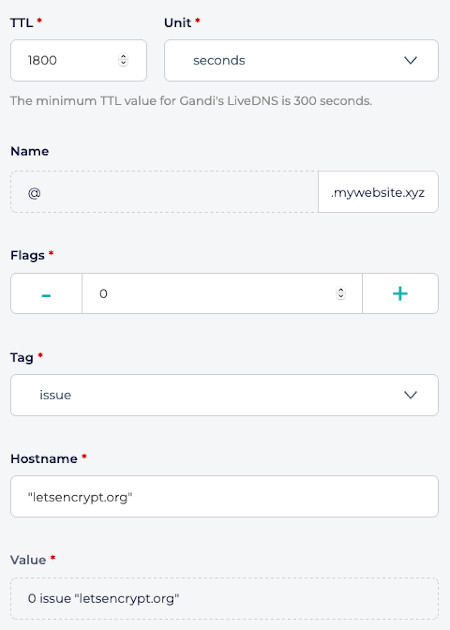
CAADNS record:- Type:
CAA - Name: empty or
@(depending on the DNS provider) - Flags:
0 - Tag:
issue - Value:
letsencrypt.orgor"letsencrypt.org"
GoDaddy Example:
Gandi Example:
Learn more on:
- How to add a CAA record on Gandi
- How to add a CAA record on Godaddy
- How to add a CAA record on AWS
- How to add a CAA record on NameCheap
Verify your CAA configuration. We recommend the following CAA lookup tools:
By default, some DNS service providers add
CAADNS record(s), while others do not allow the creation ofCAADNS records and therefore allow any CA to generate certificates.Learn more about CAA DNS records: Let’s Encrypt, Wikipedia, Gandi, and eff.org
- Type:
Domain Control Validation
Before Edgio may issue a certificate request on your behalf, we require that you validate your control over each of your hostnames by adding a CNAME record. From your DNS service provider, add the following CNAME DNS entry for each desired hostname:
-
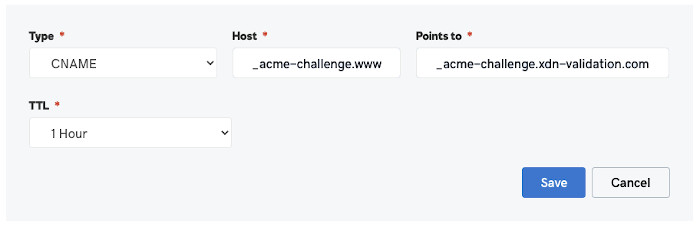
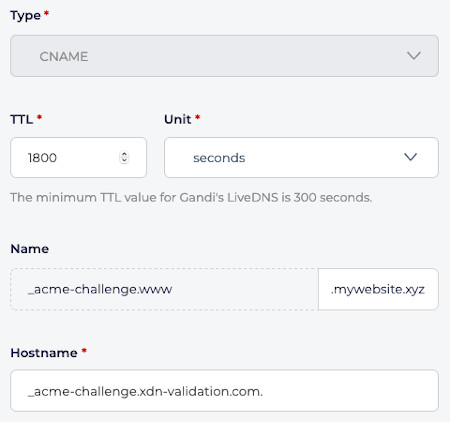
Host:
_acme-challenge.<HOSTNAME>Example:
If your hostname is
cdn.example.com, then you would set it to_acme-challenge.cdn.example.com. -
Value:
_acme-challenge.xdn-validation.com
GoDaddy Example:
Gandi Example:
Verify each CNAME record using your preferred tool. For example, you can use any of the following tools:
-
Command line: Run the following command:
Bash1# Run the following 'dig' command to verify the presence of the '_acme-challenge.' CNAME :2dig +short cname _acme-challenge.<your-domain>34# For example:5dig +short cname _acme-challenge.mywebsite.xyzExpected result for the DNS query:
1_acme-challenge.xdn-validation.com.
If you use multiple domains for your website, like mywebsite.xyz and www.mywebsite.xyz, you will have to make sure that the _acme-challenge DNS record has been added for both domains:
1_acme-challenge.mywebsite.xyz -> _acme-challenge.xdn-validation.com.2_acme-challenge.www.mywebsite.xyz -> _acme-challenge.xdn-validation.com.
If you have previously used Let’s Encrypt to generate certificates for your hostnames, you should verify that all _acme-challenge.<HOSTNAME> TXT records have been removed.
Learn more about DNS TXT domain control.
TLS Certificate Verification
Once the above requirements are met, you should verify that a TLS certificate for each of your hostnames has been generated.
To verify TLS certificate creation
-
From the Edgio Developer console, click Settings to load the Settings page. Find the TLS Certificate section.
-
Review the TLS status for each of your hostnames.
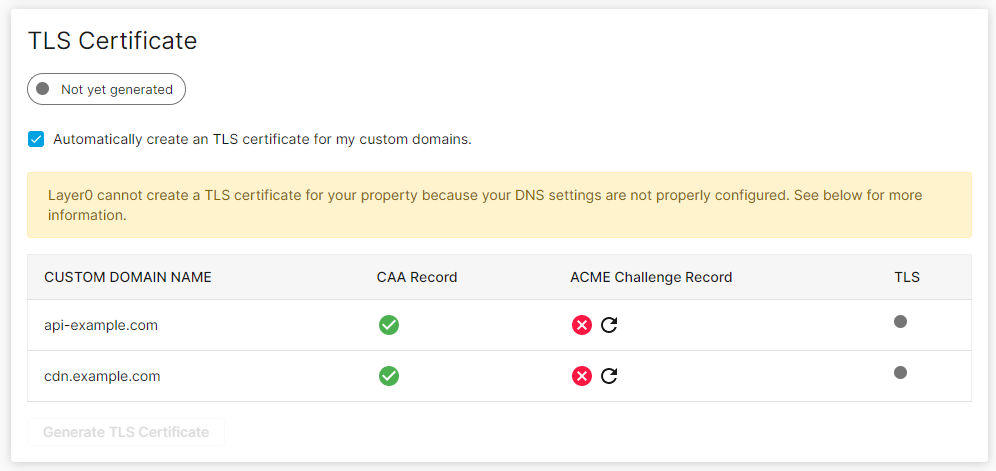
-
If a TLS certificate has not yet been generated, you may manually generate it by clicking
 under the ACME Challenge Record column.
under the ACME Challenge Record column.Edgio will generate a TLS certificate for that hostname within a few minutes.
-
Wait a few minutes and then verify that a certificate was created for that hostname.
Manually Creating a TLS Certificate
Skip this section if you plan on using autogenerated TLS certificate or if you already have an existing TLS certificate that you plan to upload.
TLS certificates are issued by Certificate Authorities (CA) based on your Certificate Signing Request (CSR). Although a single command generates a CSR and a private key, you should only share your CSR with the CA. You should also securely store your private key.
The following procedure indicates how to create a CSR and a private key with OpenSSL. OpenSSL is an open-source toolkit for the TLS protocol. We recommend using OpenSSL because it ensures that your private key will only be stored locally on your infrastructure.
Review your CA’s documentation to check for additonal requirements or a custom certification workflow.
To generate a CSR and a private key
-
From the command line, verify that OpenSSL is installed:
- MacOS: Install it by using
brewpackage manager (e.g.,brew install openssl). - Windows: Install it by using
Chocolateypackage manager (e.g.,choco install openssl). - Linux/Unix: Install it by running the built-in OS package manager (e.g.,
apt-get install openssl,apk add openssl, and so on).
- MacOS: Install it by using
-
Go to the directory of your choice and create a configuration file (e.g.,
edgio_cert.conf) based on this template:1[req]2default_bits=20483distinguished_name = req_distinguished_name4req_extensions = v3_req56[req_distinguished_name]7countryName=Country Name (2 letter code)8countryName_default=US9stateOrProvinceName=State or Province Name (full name)10stateOrProvinceName_default=California11localityName=Locality Name (e.g., city)12localityName_default=San Francisco13organizationName=Organization Name (e.g., company)14organizationName_default=YourCompanyName15commonName=Fully Qualified Domain Name (FQDN) e.g., www.your-company-name.com16commonName_default=www.your-company-domain.com1718[v3_req]19subjectAltName=@alt_names2021[alt_names] # Other domains: apex domain, wildcard domain for staging and dev, and so on22DNS.1=*.your-main-domain.com23DNS.2=*.your-dev-domain.com24DNS.3=your-apex-domain.com25# And so onReplace the country, state/province, locality, organization name, and Common Name (CN). Set the CN to your hostname’s fully qualified domain name (e.g.,
cdn.example.com).Edgio strongly encourages the use of wildcard certificates. However, if you are not using a wildcard certificate, then you will need to add the remaining hostnames into the
alt_namessection. -
Run the following command:
Bash1openssl req -out edgio.csr -newkey rsa:2048 -nodes -keyout edgio.key -config edgio_cert.conf -batchThis should generate your CSR in
edgio.csrand private key inedgio.key.If you want OpenSSL to ask you for each different input, remove the
-batchoption and re-run the command. -
Verify your CSR contains the expected domains by running the following command:
Bash1openssl req -in edgio.csr -noout -text | grep DNS -
Read the CSR (e.g.,
cat edgio.csr) or copy it to your clipboard (on OSX,cat edgio.csr | pbcopy) and send it to your CA for certification.
Uploading Your Certificate
Uploading a TLS certificate requires:
- An Enterprise account. Contact your account manager or our sales department at 1 (866) 200 - 5463 to upgrade your account.
- The
Adminrole within your team. - A certificate issued by a CA.
- The intermediate certificates (IC) used by the CA, including the CA’s signing certificate.
- The private key that was generated with the CSR.
To upload your TLS certificate
-
From the Edgio Developer console, click Settings to load the Settings page. Find the TLS Certificate section.
-
Clear the Automatically create an TLS certificate for my custom domains. option.
-
Copy the certificate, intermediate certificates, and the private key into the corresponding options.
The private key is non-public data and must not be shared with parties other than Edgio. Edgio securely stores your private key. It is never shown in the Edgio Developer console and it is only used to provision parts of the infrastructure that are used to terminate TLS connections.
-
Click Changes Saved.
After which, the status of the TLS certificate will update to Activating.

After the certificate is activated, its status becomes Active.

Certificate activation should take a few minutes. Contact technical customer support if the status does not become Active within an hour.

